
Product
Microsoft’s WFP API, and How We Use It At Golden Frog
One of our software engineers offers a high level overview of WFP, and how we integrate this technology into our products.
What is WFP?
WFP is Microsoft’s API to the network stack. It stands for “Windows Filtering Platform.”
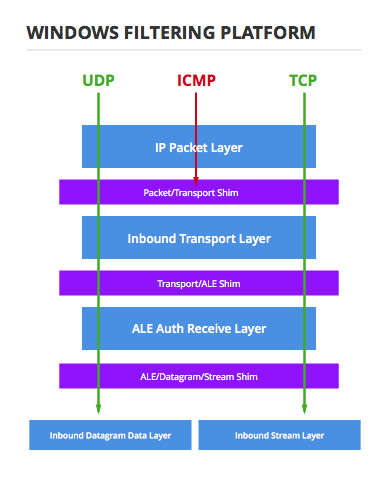
The primary unit of organization in WFP is the concept of a Layer. When network traffic traverses the network stack in Windows, it conceptually follows a path through a set of layers where the path is determined by the type of traffic it is.
Connecting the layers are Shims, or kernel components that move traffic between layers and act on the filtering decisions made in the layers. It is the decision made by the shims that determine which layers a particular packet of network traffic traverses.
Within the layers are Filters that match specific traffic, based on a set of conditions, and flag the traffic to be permitted or blocked upon leaving the current layer.
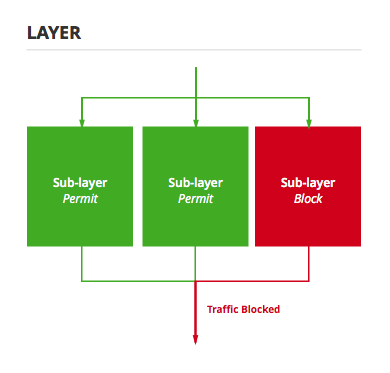
Filters are organized into layers and sublayers. Sublayers can be thought of as the components of a layer that actually hold filters, or as an attribute of filters since the sublayer is registered globally rather than on a per-layer basis. Either way you want to visualize it, when traffic is evaluated in a particular layer every sublayer is evaluated, and if any sublayer flags the traffic to be blocked, it is dropped by the shim on its way out of the layer.
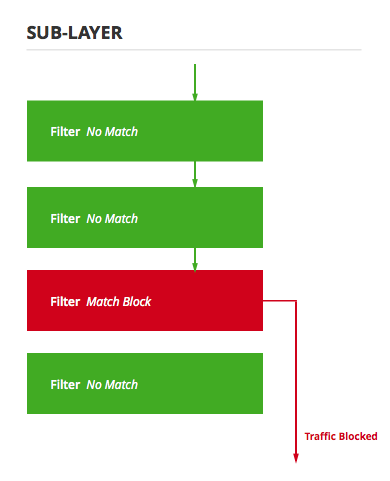
Within a sublayer not all filters are guaranteed to be evaluated. Specifically, they are evaluated in order of highest weight to lowest weight where weight is a value given to the filter at the time it is created. If a filter flags the traffic to be blocked or permitted, that is the decision of that sublayer and no further filters in the sublayer are evaluated.
How Golden Frog Uses WFP
Golden Frog utilizes WFP for its Kill Switch, DNS leak protection, and IPv6 leak protection features. Here’s what we do.
We make a custom sublayer for each feature. This means that if any feature wants to block the traffic, it will be blocked even if explicitly allowed by another feature or allowed by another piece of software (like Windows firewall).
We put high priority filters in to allow the traffic we want to allow. These are the exception, and apply to types of traffic that we want to allow even though they match the general description of the traffic we are blocking. For example: permitting loopback traffic over IPv6 in the IPv6 leak protection filter, permitting connections to our VPN servers and DHCP in the Kill Switch feature, and allowing connection to your specified VPN DNS server in the DNS leak protection feature.
We put lower priority filters in to block the traffic we want to block. These are the main deal. Kill Switch has filters that block all traffic, DNS leak protection has filters that block all DNS traffic and IPv6 leak protection has filters that block all IPv6 traffic.
Since we are using our own sublayers, if the final result of those filters is to block the traffic, it is dropped by the shim when leaving that layer. Then, all that’s left is to choose some layers where we can make all of those filters and intercept all traffic.
Like this post? Leave a comment below. And be sure to keep an eye out for more technical blogs from our development team coming soon!

